What Does a Good Risk Register Look Like?
A risk register, or risk log, is an effective tool to identify, analyze, mitigate, and manage potential project risks and opportunities that can affect project outcomes, including business, cost, schedule, production, safety, environment, and corporate image. When major threats are not identified early enough, it increases the likelihood of costly surprises and lengthy delays materializing later in the life cycle. Therefore, the risk register should be created in the early stages of business planning and updated throughout the project life cycle to help project teams understand, monitor, and make informed decisions about project risks.
Why Are Risk Registers Important?
The use of risk analysis techniques by project teams, including risk registers, is statistically linked to better project outcomes.[1] As shown below, using a risk register lowers cost growth; speeds up cycle time, execution, and startup; and reduces problems after startup.
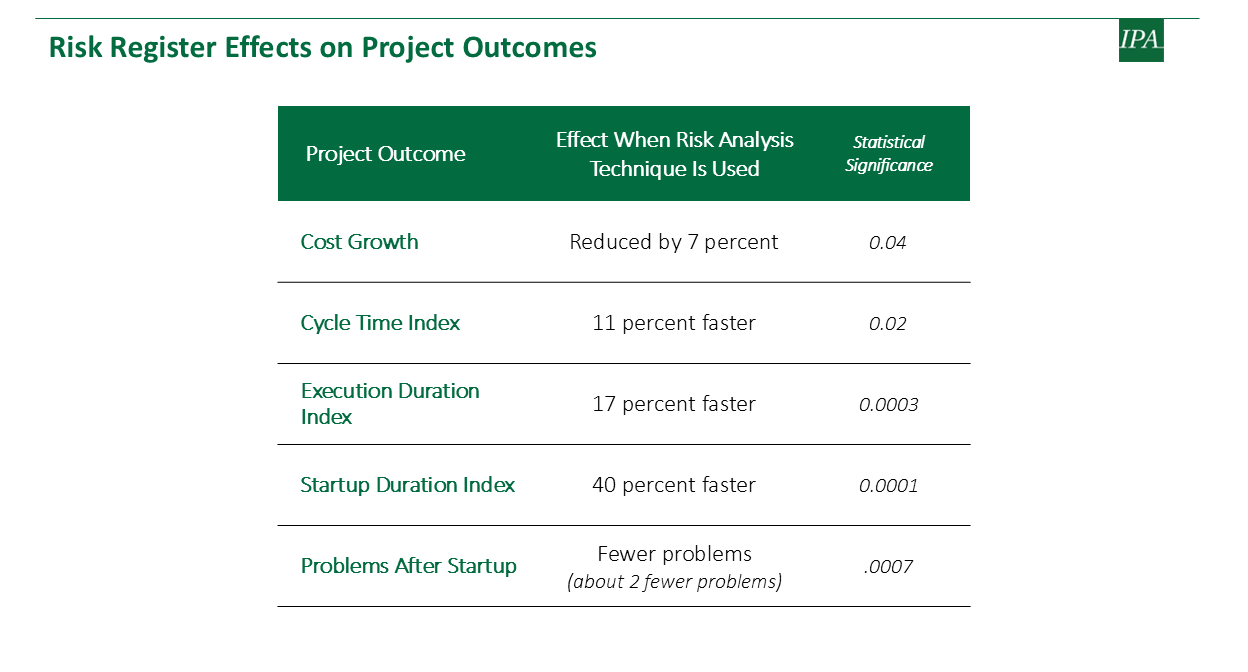
Although nearly every project team today does a risk analysis (94 percent of teams), only 17 percent of project teams develop comprehensive, truly useful risk registers/risk management plans.
How to Develop a Good Risk Register
A comprehensive risk register (1) identifies the risks a project faces, (2) analyzes and evaluates the risk identified, and (3) includes steps for the team to mitigate and manage the risks.
Identify Risks
The first step in developing a comprehensive risk register is to identify the risks the project faces. There are many tools that can be used to identify risks, including checklists, brainstorming, expert and team member interviews, exploring and reviewing historical data, and a SWOT (strengths, weaknesses, opportunities, and threats) analysis.
Risk Categories Include:
- Business Strategy
- Execution
- Project Location
- Health, Safety, & Environmental
- Project Definition
- Operation
- Communication
- Technology
Risk identification is often done as part of a workshop or series of workshops, especially for generating the initial risk register. However, identifying risks should be a continuous process, with individuals raising risks as they are perceived throughout the project life cycle. In addition, risk identification should be a multiple discipline exercise to capture all risk sources. Examples of risk categories are shown below. Each category can include many risks. For example, execution risks include scope creep, late changes canceling out project definition efforts, shutdown timing changes, underground obstacles, and more.
Evaluate Risks
Once risks are identified, the next step is to evaluate them and then rank and prioritize them. Risk classification defines the level of risk by considering the risk’s probability or likelihood of occurring and its severity.
Ranking and prioritizing risks allows management to develop a strong understanding of the project’s “risk picture” and to prioritize resources to manage the risks.
Mitigate Risks
After potential project risks are identified and analyzed, several approaches can be taken to address the risk (i.e., to decide what should be done about the identified risks, when, and by whom). For example, can the probability of occurrence be reduced? Can the risk be shared or transferred? How can the risk be avoided all together? Or is the risk acceptable as is?
Having decided on an approach to address the risk, the team should build a risk management plan that must be SMART—Specific, Measurable, Actionable, Realistic, and Time-Based. It should include:
- Assignment of a risk owner
- Development of a response
- Action horizons (timing of risk management activity)
- Base plan versus contingency planning
- Risk communication/reporting
- Monitoring of each risk or opportunity status and retirement when the window of opportunity passes
- Rolling action plan forward
- (Re)assessment: re-definition, re-planning, or neither
Putting a Good Risk Register to Use
A risk register must be a “live” document to be useful. That is, all of the steps above—identifying, evaluating, and mitigating risks—should be done throughout the project’s life cycle. Having a well-prepared risk register that is not used or updated degrades its value.
Risk register updates often decrease as the project workload increases and the project progresses through its life cycle. To be effective, the risk register needs to be updated regularly with risks added, dropped, or modified as needed to ensure all risks are effectively handled. The key to monitoring and controlling risks is being proactive and staying ahead of risks. Otherwise, the risk register becomes useless for the risks that were not mitigated/closed at authorization.
The burden of keeping the register current can be reduced by only including risks that are severe (or opportunistic) enough to monitor. Because tracking all risks on a project can lead to the team having many documents and extensive data, it is important that the risk register be maintained as a summary tool with clear links to the underlying information. The risk register should be as streamlined as much as possible, so that stakeholders can more easily understand and support the team in managing the risks. Finally, to avoid the update problems, project managers should issue a detailed risk bulletin according to the project’s size and this should be part of the progress reports.
IPA’s Risk Register Generator
In our decades working directly with owner project teams, IPA has observed that risk assessments are often too narrowly focused, do not involve the right people, and do not leverage historical industry data. As result, major threats to a project’s viability are often not identified early enough to properly address the risk.
IPA developed the Risk Register Generator specifically to address these gaps. Leveraging the millions of real-life lessons learned as recorded in IPA’s proprietary database of 24,000+ projects, the Risk Register Generator can produce a definitive risk register—including mitigation strategies—for any industrial project well before the core project team is even formed.
Complete the form below to learn more about how IPA’s Risk Register Generator takes the guesswork out of risk identification and mitigation.
[1] Edward Merrow and Chris Giguere, Effectiveness of Project Risk Analysis and Mitigation Techniques, IBC 2007, IPA, March 2007.